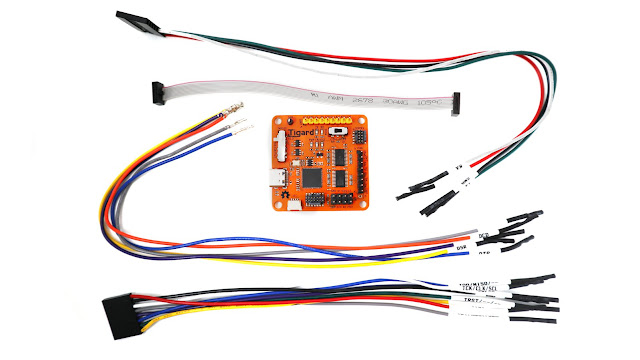
Tigard FT232H Board connectons to a Raspberry Pi 4B for GDB and OpenOCD operation
Tigard FT232H Board connectons to a Raspberry Pi 4B for GDB and OpenOCD operation
- https://www.crowdsupply.com
- https://www.crowdsupply.com/press/tigard Tigard Board Press Release
- https://www.crowdsupply.com/securinghw/tigard Securing Hardware Github directions
- https://github.com/tigard-tools/tigard Github hookup directions and source code
- https://www.electronics-lab.com/tigard-is-here-to-bust-open-any-embedded-physical-interface-you-can-find/ Electronics Lab short write up with GREAT Photo of Tigard Board.
- https://github.com/tigard-tools/tigard#jtag-debug-on-jtag-or-cortex-header Github Jtag setup of Tigard board. ( city of Tigard Oregon )
- https://embeddedsandbox.com/wordpress/my-raspberry-pi-4-jtag-setup-part-1-introduction/ Part 1 Software, of My Raspberry Pi 4 JTAG setup
- https://embeddedsandbox.com/wordpress/my-raspberry-pi-4-jtag-setup-part-2-the-hardware-setup/ Part 2 Hardware, of My Raspberry Pi 4 JTAG setup
- https://pinout.xyz/pinout/jtag Raspi 4B JTAG pinout 40 pin header, Alt4 Alt5
- https://www.eejournal.com/industry_news/tigard-easy-to-use-open-source-hardware-hacking-tool-now-available-from-crowd-supply/ EE Journal article on easy to use Tigard board.
- https://medium.com/@0xNoor/setup-openocd-with-jtag-uart-on-raspberry-pi-4-using-ft232h-da05ca01c693
- Great step by step setup of OpenOCD
- https://macoy.me/blog/programming/RaspberryPi5Debugging Very Good JTAG
- https://sysprogs.com/VisualKernel/tutorials/raspberry/jtagsetup/ Older for Raspi 1 & 3
- setup with 26 pin header.
- https://projects-raspberry.com/preparing-raspberry-pi-for-jtag-debugging/ Older for Raspi 1 & 3, but with great documentation of GPIOS and Alt4 , Alt5 diagrams
- https://elinux.org/RPi_HardwareHistory Raspberry Pi Hardware History information
15 TRST GPIO22 D4
NC SRST Not Used D5
16 RTCK GPIO23 D7
https://hackaday.com/2017/12/11/the-ibm-pc-that-broke-ibm/#comment-6734969
Convert your Raspberry Pi 2/3/4 into a networked JTAG debugger!
When developing embedded projects, I find it extremely helpful to have a hardware debugging tool available. The Black Magic probe works great for ST parts, but I often find myself reaching for a Raspberry Pi and OpenOCD for more flexibility. Unfortunately, that usually turns into a second project of looking for the proper combination of cables that will convert from the .1" headers on the RPi to the 1.27mm pins on our boards. So we decided solve the problem once and for all with the JTAG hat! The hat includes both the mini 1.27mm ARM Cortex header, along with larger 0.1" headers for easy connection to boards with older or no pins. While we were at it, we also added level converters/buffer drivers to make it possible to program devices at other voltages such as 1.8V or 5V. As a bonus, we also added a level-shifted UART interface for communicating with the target device, as well as a current sensor for measuring the power drawn by the target.
The JTAG Hat is designed to work with OpenOCD, and provides a .05" 10-pin Cortex Debug Connector, with pins to support debugging devices with either a JTAG (TCK/TMS/TDI/TDO) or SWD (SWDIO/SWDCLK) programming interface. A traditional .1, 20-pin JTAG header is also provided, which can be used with 0.1" jumper wires for more flexibility.
https://wrongbaud.github.io/posts/stm-xbox-jtag/ Good articles about reverse engineering software from a device like an XBOX controller
https://engineer.john-whittington.co.uk/electronics/2023/07/30/minnow-usbc-dam-tool.html USBC debug accesory mode (DAM) over usb-C
https://hackaday.com/2022/02/24/an-unbusy-usb-c-port-doubles-up-for-jtag-programming/ Hackaday article on debugging over USB-C
JTAG OPENOCD files and setup from MX Linux (okay I cheated a little bit)
Configuring the
Raspberry Pi 4
A critical part of setting everything up is getting the RPi4 boot up setting correct. This bit me when I first get started because I am used to embedded systems where the default reset state is to have JTAG and UART enabled. This is not the case with RPi4. I'm guessing this is because most folks can just monitor and keyboard into the system.
On the SDCard of the RPi4 there is a file in the BOOT partition called config.txt.
This is the file that the RPi4 boot loader reads to setup various
peripherals before the kernel is kicked off. For us to use the JTAG and
UART, we at a minimum the following lines added to the config.txt file:
gpio=22-27=np
enable_jtag_gpio=1
enable_uart=1Once added, save and reboot.
adapter speed 1000
ftdi_vid_pid 0x0403 0x6010
ftdi_channel 0
transport select jtag
# Specifies the initial values of the FTDI GPIO data and direction registers.
# Each value is a 16-bit number corresponding to the concatenation of the
# high and low FTDI GPIO registers. The values should be selected based on
# the schematics of the adapter, such that all signals are set to safe levels
# with minimal impact on the target system. Avoid floating inputs,
# conflicting outputs and initially asserted reset signals.
ftdi_layout_init 0x0000 0x000b
set _CHIPNAME bcm2711
set _DAP_TAPID 0x4ba00477
transport select jtag
reset_config trst_and_srst
telnet_port 4444
jtag newtap auto0 tap -irlen 4 -expected-id $_DAP_TAPID
dap create auto0.dap -chain-position auto0.tap
set CTIBASE {0x80420000 0x80520000 0x80620000 0x80720000}
set DBGBASE {0x80410000 0x80510000 0x80610000 0x80710000}
set _cores 4
set _TARGETNAME $_CHIPNAME.a72
set _CTINAME $_CHIPNAME.cti
set _smp_command ""
for {set _core 0} {$_core < $_cores} { incr _core} {
cti create $_CTINAME.$_core -dap auto0.dap -ap-num 0 -baseaddr [lindex $CTIBASE $_core]
set _command "target create ${_TARGETNAME}.$_core aarch64 \
-dap auto0.dap -dbgbase [lindex $DBGBASE $_core] \
-coreid $_core -cti $_CTINAME.$_core"
if {$_core != 0} {
set _smp_command "$_smp_command $_TARGETNAME.$_core"
} else {
set _smp_command "target smp $_TARGETNAME.$_core"
}
eval $_command
}
eval $_smp_command
targets $_TARGETNAME.0
# sudo openocd -f interface/ftdi/cjmcu-ft232h.cfg -f target/bcm2711.cfg
# SPDX-License-Identifier: GPL-2.0-or-later
# The Broadcom BCM2711 used in Raspberry Pi 4
# No documentation was found on Broadcom website
# Partial information is available in raspberry pi website:
# https://www.raspberrypi.org/documentation/hardware/raspberrypi/bcm2711/
if { [info exists CHIPNAME] } {
set _CHIPNAME $CHIPNAME
} else {
set _CHIPNAME bcm2711
}
if { [info exists CHIPCORES] } {
set _cores $CHIPCORES
} else {
set _cores 4
}
if { [info exists USE_SMP] } {
set _USE_SMP $USE_SMP
} else {
set _USE_SMP 0
}
if { [info exists DAP_TAPID] } {
set _DAP_TAPID $DAP_TAPID
} else {
set _DAP_TAPID 0x4ba00477
}
jtag newtap $_CHIPNAME cpu -expected-id $_DAP_TAPID -irlen 4
adapter speed 3000
dap create $_CHIPNAME.dap -chain-position $_CHIPNAME.cpu
# MEM-AP for direct access
target create $_CHIPNAME.ap mem_ap -dap $_CHIPNAME.dap -ap-num 0
# these addresses are obtained from the ROM table via 'dap info 0' command
set _DBGBASE {0x80410000 0x80510000 0x80610000 0x80710000}
set _CTIBASE {0x80420000 0x80520000 0x80620000 0x80720000}
set _smp_command "target smp"
for { set _core 0 } { $_core < $_cores } { incr _core } {
set _CTINAME $_CHIPNAME.cti$_core
set _TARGETNAME $_CHIPNAME.cpu$_core
cti create $_CTINAME -dap $_CHIPNAME.dap -ap-num 0 -baseaddr [lindex $_CTIBASE $_core]
target create $_TARGETNAME aarch64 -dap $_CHIPNAME.dap -ap-num 0 -dbgbase [lindex $_DBGBASE $_core] -cti $_CTINAME
set _smp_command "$_smp_command $_TARGETNAME"
}
if {$_USE_SMP} {
eval $_smp_command
}
# default target is cpu0
targets $_CHIPNAME.cpu0
Attaching with OpenOCD
Installing OpenOCD
For building OpenOCD, I would recommed to follow the steps given on this guide.
OpenOCD configuration
For FT232H, I would recommend the following configuration. This can be stored under the interface/ftdi folder or anywhere you want. Like /usr/share/openocd/scripts/interface/ft2232h-to-rpi4.cfg
# config file for generic FT232H based USB-serial adapter# TCK: D0
# TDI: D1
# TDO: D2
# TMS: D3
# TRST: D4
# SRST: D5
# RTCK: D7adapter speed 3000
# Setup driver type
adapter driver ftdi# Common PID for FT232H
ftdi vid_pid 0x0403 0x6014
ftdi layout_init 0x0078 0x017b
# Set sampling to allow higher clock speed
ftdi_tdo_sample_edge falling
ftdi layout_signal nTRST -ndata 0x0010 -noe 0x0040
ftdi layout_signal nSRST -ndata 0x0020 -noe 0x0040# change this to 'transport select swd' if required
transport select jtag
# references
# https://sourceforge.net/p/openocd/mailman/message/31617382/ 2013 post about nTRST and nSRST
# http://www.baremetaldesign.com/index.php?section=hardware&hw=jtag 404 not workingFor the raspberry pi 4B configuration, I would recommend the default which comes with OpenOCD. This is stored under the target folder at /usr/share/openocd/scripts/target file bcm2711.cfg
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi# sudo openocd -f interface/ftdi/cjmcu-ft232h.cfg
Open On-Chip Debugger 0.11.0-rc2
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
/usr/bin/../share/openocd/scripts/interface/ftdi/cjmcu-ft232h.cfg:16: Error: invalid command name "ftdi"
in procedure 'script'
at file "embedded:startup.tcl", line 26
at file "/usr/bin/../share/openocd/scripts/interface/ftdi/cjmcu-ft232h.cfg", line 16
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi# nano cjmcu-ft232h.cfg
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi# sudo openocd -f interface/ftdi/cjmcu-ft232h.cfg
Open On-Chip Debugger 0.11.0-rc2
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
/usr/bin/../share/openocd/scripts/interface/ftdi/cjmcu-ft232h.cfg:23: Error: invalid command name "ftdi"
in procedure 'script'
at file "embedded:startup.tcl", line 26
at file "/usr/bin/../share/openocd/scripts/interface/ftdi/cjmcu-ft232h.cfg", line 23
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi# nano ft2232h_to_rpi4.cfg
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi# sudo openocd -f interface/ftdi/ft2232h_to_rpi4.cfg
Open On-Chip Debugger 0.11.0-rc2
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
Warn : Transport "jtag" was already selected
Info : Listening on port 6666 for tcl connections
Info : Listening on port 4444 for telnet connections
Info : clock speed 1000 kHz
Error: JTAG scan chain interrogation failed: all ones
Error: Check JTAG interface, timings, target power, etc.
Error: Trying to use configured scan chain anyway...
Error: auto0.tap: IR capture error; saw 0x0f not 0x01
Warn : Bypassing JTAG setup events due to errors
Error: Invalid ACK (7) in DAP response
Error: JTAG-DP STICKY ERROR
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi# sudo openocd -f interface/ftdi/ft2232h_to_rpi4.cfg -f ^C
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi# sudo openocd -f interface/ftdi/ft2232h_to_rpi4.cfg -f target/bcm2711.cfg
Open On-Chip Debugger 0.11.0-rc2
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
Warn : Transport "jtag" was already selected
Info : Listening on port 6666 for tcl connections
Info : Listening on port 4444 for telnet connections
Info : clock speed 3000 kHz
Error: JTAG scan chain interrogation failed: all ones
Error: Check JTAG interface, timings, target power, etc.
Error: Trying to use configured scan chain anyway...
Error: auto0.tap: IR capture error; saw 0x0f not 0x01 warn : Bypassing JTAG setup events due to errors
Error: Invalid ACK (7) in DAP response
Error: JTAG-DP STICKY ERROR
Bus 004 Device 002: ID 8087:8000 Intel Corp. Integrated Rate Matching Hub
Bus 004 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 002 Device 002: ID 8087:8008 Intel Corp. Integrated Rate Matching Hub
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 003 Device 002: ID 04e8:4001 Samsung Electronics Co., Ltd PSSD T7
Bus 003 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub
Bus 001 Device 003: ID 8087:07dc Intel Corp. Bluetooth wireless interface
Bus 001 Device 045: ID 0403:6010 Future Technology Devices International, Ltd FT2232C/D/H Dual UART/FIFO IC
Bus 001 Device 008: ID 046d:c52b Logitech, Inc. Unifying Receiver
Bus 001 Device 005: ID 093a:2510 Pixart Imaging, Inc. Optical Mouse
Bus 001 Device 036: ID 1d50:6018 OpenMoko, Inc. Black Magic Debug Probe (Application)
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi#
[2413977.537762] ftdi_sio ttyUSB1: FTDI USB Serial Device converter now disconnected from ttyUSB1
[2413977.537787] ftdi_sio 1-3:1.1: device disconnected
[2413980.327068] usb 1-3: new high-speed USB device number 45 using xhci_hcd
[2413980.480352] usb 1-3: New USB device found, idVendor=0403, idProduct=6010, bcdDevice= 7.00
[2413980.480359] usb 1-3: New USB device strings: Mfr=1, Product=2, SerialNumber=3
[2413980.480363] usb 1-3: Product: Tigard V1.1
[2413980.480366] usb 1-3: Manufacturer: SecuringHardware.com
[2413980.480369] usb 1-3: SerialNumber: TG110197
[2413980.485296] ftdi_sio 1-3:1.0: FTDI USB Serial Device converter detected
[2413980.485335] usb 1-3: Detected FT2232H
[2413980.485497] usb 1-3: FTDI USB Serial Device converter now attached to ttyUSB0
[2413980.486880] ftdi_sio 1-3:1.1: FTDI USB Serial Device converter detected
[2413980.486917] usb 1-3: Detected FT2232H
[2413980.487093] usb 1-3: FTDI USB Serial Device converter now attached to ttyUSB1
[2415251.578221] ftdi_sio ttyUSB0: FTDI USB Serial Device converter now disconnected from ttyUSB0
[2415251.578260] ftdi_sio 1-3:1.0: device disconnected
root@mx16-Klik:/usr/share/openocd/scripts/interface/ftdi#
Success with Tigard Board and Openocd
Started with out the USB cable connected from MXLinux development computer to the target Raspberry Pi 4B sbc
Open On-Chip Debugger 0.11.0-rc2
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
DEPRECATED! use 'adapter driver' not 'interface'
jtag
Info : Listening on port 6666 for tcl connections
Info : Listening on port 4444 for telnet connections
Error: no device found
Error: unable to open ftdi device with vid 0403, pid 6010, description '*', serial '*' at bus location '*'
Check for connect USB adapters for the FTDI FT2232H board 0x0403 : 0x6010. Not found below!
root@mx16-Klik:/usr/share/openocd/scripts/target# lsusb
Bus 004 Device 002: ID 8087:8000 Intel Corp. Integrated Rate Matching Hub
Bus 004 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 002 Device 002: ID 8087:8008 Intel Corp. Integrated Rate Matching Hub
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 003 Device 002: ID 04e8:4001 Samsung Electronics Co., Ltd PSSD T7
Bus 003 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub
Bus 001 Device 003: ID 8087:07dc Intel Corp. Bluetooth wireless interface
Bus 001 Device 008: ID 046d:c52b Logitech, Inc. Unifying Receiver
Bus 001 Device 005: ID 093a:2510 Pixart Imaging, Inc. Optical Mouse
Bus 001 Device 036: ID 1d50:6018 OpenMoko, Inc. Black Magic Debug Probe (Application)
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
FTDI FT2232H Tigard Board found here below 0x0403 : 0x6010
Bus 004 Device 002: ID 8087:8000 Intel Corp. Integrated Rate Matching Hub
Bus 004 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 002 Device 002: ID 8087:8008 Intel Corp. Integrated Rate Matching Hub
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 003 Device 002: ID 04e8:4001 Samsung Electronics Co., Ltd PSSD T7
Bus 003 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub
Bus 001 Device 003: ID 8087:07dc Intel Corp. Bluetooth wireless interface
Bus 001 Device 053: ID 0403:6010 Future Technology Devices International, Ltd FT2232C/D/H Dual UART/FIFO IC
Bus 001 Device 008: ID 046d:c52b Logitech, Inc. Unifying Receiver
Bus 001 Device 005: ID 093a:2510 Pixart Imaging, Inc. Optical Mouse
Bus 001 Device 036: ID 1d50:6018 OpenMoko, Inc. Black Magic Debug Probe (Application)
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Now use the command line for OpenOCD with 2 files from /usr/share/openocd/scripts directory
Open On-Chip Debugger 0.11.0-rc2
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
DEPRECATED! use 'adapter driver' not 'interface'
jtag
Info : Listening on port 6666 for tcl connections
Info : Listening on port 4444 for telnet connections
Info : clock speed 3000 kHz
Info : JTAG tap: bcm2711.cpu tap/device found: 0x4ba00477 (mfg: 0x23b (ARM Ltd), part: 0xba00, ver: 0x4)
Info : bcm2711.cpu0: hardware has 6 breakpoints, 4 watchpoints
Info : bcm2711.cpu1: hardware has 6 breakpoints, 4 watchpoints
Info : bcm2711.cpu2: hardware has 6 breakpoints, 4 watchpoints
Info : bcm2711.cpu3: hardware has 6 breakpoints, 4 watchpoints
Info : starting gdb server for bcm2711.cpu0 on 3333
Info : Listening on port 3333 for gdb connections
Info : starting gdb server for bcm2711.cpu1 on 3334
Info : Listening on port 3334 for gdb connections
Info : starting gdb server for bcm2711.cpu2 on 3335
Info : Listening on port 3335 for gdb connections
Info : starting gdb server for bcm2711.cpu3 on 3336
Info : Listening on port 3336 for gdb connections
File interface/ftdi/tigard-jtag.cfg
# /usr/share/openocd/scripts/interface/ftdi/tigard-jtag.cfg
# A configuration file for the Tigard Board opneocd -f tigard-jtag.cfg
# interface ftdi
adapter driver ftdi
ftdi_vid_pid 0x0403 0x6010
ftdi_channel 1
adapter speed 2000
ftdi_layout_init 0x0038 0x003b
ftdi_layout_signal nTRST -data 0x0010
ftdi_layout_signal nSRST -data 0x0020
transport select jtag
File target/bcm2711.cfg
# sudo openocd -f interface/ftdi/cjmcu-ft232h.cfg -f target/bcm2711.cfg
# sudo openocd -f interface/ftdi/ft2232h-to-rpi4.cfg -f target/bcm2711.cfg
# sudo openocd -f interface/ftdi/tigard-jtag.cfg -f target/bcm2711.cfg
# SPDX-License-Identifier: GPL-2.0-or-later
# The Broadcom BCM2711 used in Raspberry Pi 4
# No documentation was found on Broadcom website
# Partial information is available in raspberry pi website:
# https://www.raspberrypi.org/documentation/hardware/raspberrypi/bcm2711/
if { [info exists CHIPNAME] } {
set _CHIPNAME $CHIPNAME
} else {
set _CHIPNAME bcm2711
}
if { [info exists CHIPCORES] } {
set _cores $CHIPCORES
} else {
set _cores 4
}
if { [info exists USE_SMP] } {
set _USE_SMP $USE_SMP
} else {
set _USE_SMP 0
}
if { [info exists DAP_TAPID] } {
set _DAP_TAPID $DAP_TAPID
} else {
set _DAP_TAPID 0x4ba00477
}
jtag newtap $_CHIPNAME cpu -expected-id $_DAP_TAPID -irlen 4
adapter speed 3000
dap create $_CHIPNAME.dap -chain-position $_CHIPNAME.cpu
# MEM-AP for direct access
target create $_CHIPNAME.ap mem_ap -dap $_CHIPNAME.dap -ap-num 0
# these addresses are obtained from the ROM table via 'dap info 0' command
set _DBGBASE {0x80410000 0x80510000 0x80610000 0x80710000}
set _CTIBASE {0x80420000 0x80520000 0x80620000 0x80720000}
set _smp_command "target smp"
for { set _core 0 } { $_core < $_cores } { incr _core } {
set _CTINAME $_CHIPNAME.cti$_core
set _TARGETNAME $_CHIPNAME.cpu$_core
cti create $_CTINAME -dap $_CHIPNAME.dap -ap-num 0 -baseaddr [lindex $_CTIBASE $_core]
target create $_TARGETNAME aarch64 -dap $_CHIPNAME.dap -ap-num 0 -dbgbase [lindex $_DBGBASE $_core] -cti $_CTINAME
set _smp_command "$_smp_command $_TARGETNAME"
}
if {$_USE_SMP} {
eval $_smp_command
}
# default target is cpu0
targets $_CHIPNAME.cpu0
Wow, look at that, finally connects and work with the proper configuration files!! tigard-jtag.cfg bcm2711.cfg
OpenOCD CLI over Telnet
Once we know we have OpenOCD up and running successfully, we can telnet into its CLI interface to run various JTAG commands or pre-defined routines.
telnet 127.0.0.1 4444
Running scan_chain is a quick and simple way to check if you are getting any communication over your JTAG TAP.
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
Open On-Chip Debugger
> scan_chain
TapName Enabled IdCode Expected IrLen IrCap IrMask
-- ------------------- -------- ---------- ---------- ----- ----- ------
0 auto0.tap Y 0x4ba00477 0x4ba00477 4 0x01 0x03
Welcome to devicetree.org
If you are looking for the devicetree specification you’ve come to the right place!
Current release is v0.4
Devicetree.org is a community effort by many companies and individuals to facilitate the future evolution of the Devicetree Standard.
The devicetree is a data structure for describing hardware. Rather than hard coding every detail of a device into an operating system, many aspects of the hardware can be described in a data structure that is passed to the operating system at boot time. The devicetree is used by OpenFirmware, OpenPOWER Abstraction Layer (OPAL), Power Architecture Platform Requirements (PAPR) and in the standalone Flattened Device Tree (FDT) form.
The devicetree specification provides a full technical description of the devicetree data format and best practices.
Sample DTS file and use of dtc compiler to create a .dtbo overlay file; cp to /boot/overlay
A wealth of information to read, study, and absorb about DTS files and DTC compilers.
A description of Device Tree DT and overlays in the description
- Example: Editing MCP2515 overlay to work with new SPI6
What is the Device Tree?
Roughly speaking the Device Tree describes all the hardware of a device in a tree format. It is especially used for anything that can't be discovered automatically like serial interfaces, internal memory, oscillators, ... (in contrast to e.g. USB or PCI devices). As the Raspberry Pi has a lot of GPIO headers exposed, additional devices can be added that the current device tree doesn't know about. That's where overlays come into play.
The default base device tree source file for the RPI4 B can be found in the kernel sources in the raspberrypi/linux under linux/arch/arm/boot/dts/bcm2711-rpi-4-b.dts. This is the source file for the board, which is based itself on the source file for the SoC linux/arch/arm/boot/dts/bcm2711.dtsi.
What is an overlay?
Overlays are applied to the base device tree at a later point to change it, usually to add a device, or to configure/enable one that is already present in the base device tree.
For example: the overlay spi5-1cs-overlay.dts configures the spi5 node already present in the device tree to enable it with one CS pin and a spidev device.
All available overlays can be found in the /boot/overlays directory. Albeit already compiled.

Comments
Post a Comment